

Introduction
I worked in I.T. for 30 years, the last 8 of which I spent leading the technical service team at St. Norbert College. As you can imagine, we saw everything. We helped students, staff, and faculty with a wide range of questions, problems, and often times just practical assistance figuring out technology. And while we managed all of the computers that the college owned, we also provided support for thousands of students who owned their own computers. And not just computers. We helped out with tablets, phones, TVs, and all those new smart devices that college students receive for Christmas.
With all of these devices and all of that expertise that my team maintained, the most important issue that we ever helped with was the security of peoples' accounts. If you allow intruders access to your accounts (email, banking, streaming TV, etc) then nothing else you do will matter. And we provided this assistance to people with all levels of knowledge about technology.
This stuff can be confusing and even overwhelming. Technology is always changing. But you have to stay on top of it if you're going to keep your accounts safe.
So, with a tip of my hat to Chris, Neil, Donny, Annicka, Kheenan, and Casey, my incredible team over the years who had all the real skills and did all the hands-on work with our customers, I'm offering these tips to help you keep your online accounts secure.
I've laid out this article in sections, so that you can return and find what you're looking for quickly.
Think of the companies with which you have accounts. Start by simply checking with those companies to see what they recommend for maintaining the security of your account with them. Here are some examples:
I'm going to offer more detail about a couple of accounts here, just to give you an idea of the kinds of things you should be looking for with any account.
If you have a Google account, visit their security page. Use the tools provided on that page to review your activity and devices. If you find activity or a device that you don't recognize, follow Google's steps to click on it and have them log you off of that device (no matter where it is).
Note that if you see something and you're just not sure about it, go ahead and have Google log you off of it anyway. Worst case is that maybe it was a TV or something where you logged into YouTube in the past (for example) and you may just have to log back in again on that device. However, if you do see something and you have absolutely no recollection of that activity, you should not only have Google log you off of that device but also change your Google password.
Visit their People & sharing page. Look at the people who you're sharing data with. Review the "Location sharing" settings, and be sure that everyone who can see your location is legit.
 If you suspect someone may have gained access to your email account,
you should immediately change your password (see "Password Management" below).
However, even after you do that, you should still check to see if a hacker left any remnants behind.
I'm using Gmail here as the example, but this same concept applies to any email account.
If you suspect someone may have gained access to your email account,
you should immediately change your password (see "Password Management" below).
However, even after you do that, you should still check to see if a hacker left any remnants behind.
I'm using Gmail here as the example, but this same concept applies to any email account.
Check your "sent" folder to see if any suspicious emails are being sent out from your account. Often this will happen automatically based on some rules that a hacker turned on in your settings. If you find emails in there that don't look right, look at the email address that they are being sent to. This is likely the email address of the hacker, though it's probably a throwaway address that they can quickly dump. There is nothing you can do about emails that have already been forwarded out from your account.
To make sure emails are not still being forwarded out automatically, if you're using Gmail:
Other Accounts
If your account or company name is not listed above, use this 'account security' button and I'll help you find the right info:
To gain access to any online account, you need a user ID (aka login ID) which is often assigned by the company. For example, some companies require that you use your email address as your user ID. So, generally speaking, since your user ID may not be very difficult for a hacker to guess, the real security starts with your password. If a hacker knows your password, they're in. That's 1-factor authentication.
2-factor authentication (sometimes refered to as 2 step verification) means that you need two things to get into your account instead of just one. Often this means you need your password AND your phone.
So, how does it work? It depends on the company. Some websites will prompt you for your password and then text you a code that you must enter after your password. Of course this only works if you have your phone with you to receive that text message with the code.
Other websites may require you to use an authenticator app on your phone to generate a code that you must enter after your password. Again, this would mean that you must have your phone to do that.
The idea here is that if someone does figure out your password, they still can't get into your account because they don't have your phone; they don't have that 2nd factor.
So, what's the catch? It's simple really. You MUST have your phone to login. If your employer uses 2-factor authentication and you're at work and you forgot your phone at home, tough; you won't be able to login. Period. Now, does this sound inconvenient? Sure. But that's the point. You need to have your phone.
Other types of 2-factor authentication require you to have a USB device or other physical device (instead of your phone). But the concept is the same. The idea here is that it's no longer smart to get into your account with just a user ID and password. You need a user ID and your password and your phone. And if you don't have your phone or you dropped it and it shattered, please don't get mad at your tech support folks.
So, while I strongly recommend using 2-factor authentication on your accounts that offer it, be sure you understand how it works and what it means.
There was a time when using secure websites was only recommended for online banking and websites that require a login. Those days are gone. Today, most all websites of importance offer a secure connection. And you should demand it.
Having a secure website means that all content and form submissions are encrypted when sent between your device and the server that hosts the website. Because of this, a hacker cannot intercept the data while in transit.
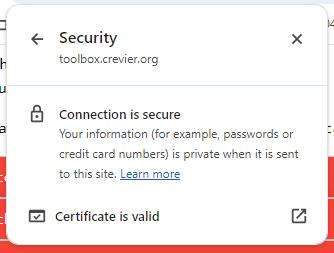
The easiest way to tell the difference is that traditional (non-secure) websites have a URL that starts with 'http:', while secure websites have a URL that starts with 'https:' (that extra "s" means "secure"). Consider this example:
https://toolbox.crevier.org/ SECURE
http://toolbox.crevier.org/ NOT SECURE
In most browsers, you can click the small icon just to the left of the URL and it'll show you information about the security of the website you're on. Go ahead and try it right now. The screenshot shown here is what Chrome shows when you click the icon while on this website. It's very easy to see if you're on a secure site.
You may wonder if viewing something insignificant like sports scores really requires a secure connection. The real answer is "perhaps not." But it's just a good idea these days to make sure all of the websites you visit are indeed secure. Web browsers like Chrome are also very good at warning you if you're attempting to view a web page that is not secure.
You should be using a software tool to manage ALL of your passwords. And the password to that tool is the only one you should have memorized.
This concept is new to many people, so I'll explain how this works. The password manager you use should have a website that you login to where you manage all of your passwords. You should also be able to manage your passwords via a corresponding mobile app on your phone; this way, you always have all of your passwords with you.
See the recommendations below to find a good password manager tool. When you create a new account with one, you'll need a password that you can memorize (this should be the only password you memorize). I suggest making it long and consisting of multiple words. Just look around your room and come up with some words. For example: stapler7mints&lamp*
Here are some practical tips on how to use any password management tool:
Creating a new account
When you create a new account on any website, you should first create an entry for that site in your password manager; enter the name and address (URL) of the site, and your login ID. Your password manager should then allow you to click a button to generate a new password. When doing this, create one that is very long (at least 20 characters) and uses a mix of upper case letters, lower case letters, numbers, and special characters. For example:
Y28TmBJyPenJdUcJxUKC7#zKV4&Wm!xwGLbvv#f2
Then go to the website where you're creating the new account. Copy and paste your login ID (often this is your email address) and your newly generated password. Note that some sites may not like your randomly generated password. For example, maybe it's too long or it has too many special characters. If this is the case, just adjust it in your password manager to match their requirements.
It's important to understand that you will never need to know or memorize this password. Read on to see how you'll use it.
Logging into a website
When you visit a website that requires you to login, open your password manager in another browser tab. Or if you're on your phone, switch over and open the password manager app. Copy your user ID and then switch back to the website and paste it. Do the same for your password. Note that since you're copying and pasting your password, YOU NEVER NEED TO KNOW IT. You don't even need to see it. This is why creating a long, nasty password like the one above works well.
The above steps may seem clunky and time-consuming, but this is how to secure your passwords. Some password managers offer additional functionality that allows them to enter your password for you (i.e. via a browser add-on), which means you may not need to switch back and forth between the website and your password manager.
Password manager recommendations
Here are a few articles that offer recommendations:
Change your current passwords
This will take some work. Perhaps a lot of work. Once you start using a good password manager, you should now visit all of your websites and change your password so that they are all unique and they fit my recommendations above. Depending on how active you are on the internet, this may take some time. Be realistic. Perhaps you have to make a plan to get all of your passwords into your password manager over the course of a few months. Fine. If that's what it takes, do it. The quicker the better, but just do it.
Tip
You can use your password manager to store other secure information too, like credit card numbers and your kids' social security numbers.
Summary
You should never know your email password. You should never know your Facebook password. This can be a difficult concept to get used to. But get used to it. A good password manager will allow you to manage all of your passwords while ensuring that each of them is unique and long and difficult to hack.
Well, maybe it wasn't.
I often seen people on Facebook say something like, "don't respond to any invites from me, I got hacked." But this is usually not true.
What probably happened is that someone saw your Facebook profile and just used all of your info (including photos) to a create a new Facebook account; a duplicate of yours. Facebook calls this an "impersonation account." That's not hacking. In other words, no one actually got a hold of your password and logged into your Facebook account (which is a good thing).
So, what should you do if this happens to you?
My Facebook account has been impersonated a couple of times, and Facebook was very good at shutting down the impersonated account as soon as I reported it. Don't try to contact Facebook or email them directly. Just use the tools they provide and they'll help.
What if your account really was hacked?
If this really did happen, this means that someone got a hold of your password (maybe it was too easy for them to guess) and they logged in as you and took over. If this happened, use Facebook's tool to report a hacked or fake account. They have a good reputation of helping when you use the tools they provide.
QR codes can be used for many purposes, the most popular of which is to link to websites. However, just like there are scams in your email Inbox that convince you to click a link to a scammer's website, a QR code can also be spoofed and send you to a site that you are not expecting (like one that asks you for your email and password). So let's first look at how it works. Here's the simple process:
The Basics
How Do You Know?
How do you know if a URL is valid? Just use common sense. For example, if you're clicking a QR code expecting to visit your favorite store's website, then that store's URL should appear. If it doesn't, don't click it.
Note that some very legitimate companies use QR code trackers. The best way to explain is with an example. Let's say Target shows a QR code in a TV commercial allowing you to take advantage of an online sale. So you scan the code on your TV and instead of the URL being 'target.com' it's actually someting like 'qr-tracker.us'. Such a tracking site allows Target to know how many people are scanning their QR codes. Even though this all could be legitimate, I would still never click on such a code. If I'm scanning a Target QR code then I expect 'target.com' to be in the URL. Period. I don't need companies tracking my usage of their QR codes, even if they say it's harmless.
Live Examples
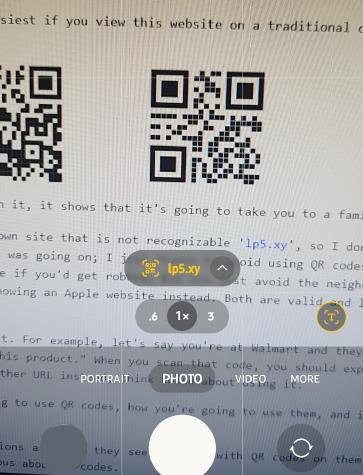
Now let's take a look at a couple of sample QR codes. To do so, it's easiest if you view this website on a traditional computer or tablet while scanning the QR codes with your phone. Just open your camera and point it at the code.


The first QR code is a valid QR code for this website. When you scan it, it shows that it's going to take you to a familiar website, 'toolbox.crevier.org'.
The second QR code takes you to a tracking site or some other unknown site that is not recognizable 'lp5.xy', so I don't recommend clicking on it. Now, based on this information alone, it's impossible to know for sure if any scamming was going on. So my recommendation is to simply avoid using QR codes that send you to unknown websites. It's kind of like avoiding a shady looking neighborhood; you don't know for sure if you'd get robbed, but you just avoid the neighborhood anyway.
Here's a good video about QR code scams:
Scams are everywhere. There are scam websites. There are scam emails. There are scam letters (via the post office). Everywhere you look, there are scams. So, what do you do?
Well, let's just start by taking a step back. What if I sent you a short email with this simple request:
"Hey buddy, please respond to this email and give me the password to your bank account."
Sounds ridiculous doesn't it? That would be easy to spot and you'd certainly not respond to it (you wouldn't would you?). Scammers know this. But let me throw a different angle at the same message. What if I instead made myself look like I'm your bank, and used what's called "social engineering" to get you to give me your password in some other clever way? This is not hacking. It doesn't even require good technical skills. No, instead, the scammer just needs good social skills. They need to know how to trick people. They need to know how to catch you off your guard and get you to do things that you really don't want to. And they're very good at it. So, back to the question, what should you do?
First, be suspicious about everything. Seriously. EVERYTHING. When you receive an email about an account that you have and they're trying to get you to click something, just don't. If it sounds like something you want to pursue, contact the company using a method that you would normally use (i.e. via website, email, phone call) and ask them if they sent that email to you. For example, you can call them on the phone or you can email them using an address you've used in the past. Or you can visit their website using a link that you have saved INSTEAD OF clicking on a link in an email.
What you really need to understand is that scammers know how we humans work, and they're very good at convincing you to do bad things. They add various angles to their communication to trick you into giving them access. The best way to proceed here it to just give you real examples of scams. I hope that by reading through these you'll be able to recognize them better.
Scam #1 - Phishing & Spoofing
One of the more common scams is when you receive an email telling you that there's a problem with your bank account and you should "click here" to resolve it. They'll often include a scare tactic like, "if you don't resolve this within 24 hours you may be locked out of your bank account." So you click their link and you get a website where you enter your user ID and password. And now, instead of getting into your bank account, you've just given your info to a scammer.
The email they sent you sure looks like the bank's email. They used your bank's colors and they even faked the email address to make it look real. That's "phishing". And when the website you visited sure looks like the bank's website, with the right colors and even the bank's logo, that's "spoofing".
Let me go one step further and give you an example of a faked email address. Consider the following two email addresses:
customersupport@mybank.com
customersupport@mybank.com.kdiek.ru
I hope you can see the differece. Now, does this mean you need to look closely at all emails that you receive from your bank? YES! In a related comparison, notice the similarity in these website addresses:
https://www.myschool.edu/
https://myschool.edu.lp4.ru/
Again, I hope you can see the differece.
Scam #2 - Situational Phishing & Spoofing
This is a version of everything I just described in Scam #1 above. Imagine if the situation I described happens the day before you're leaving on vacation? You're probably pretty busy wrapping up loose ends before you leave work. You probably still need to finish washing your clothes and packing for the trip. Yes, it's a very hectic time, but you're looking forward to two weeks off so it's all worth it. And if a hacker somehow finds out that you're traveling, they'll wait until the day before you leave to try to trick you. They'll take advantage of your situation and use that against you.
Now, imagine that your mother just passed away. Yes, that's what I said, your mother just passed away. You receive an email from your church or civic group with a very kind and gentle message expressing condolences and asking you to consider donating money to their cause. It's VERY convincing, especially since the email came from your mother's favorite charity. And they're only asking for $20. So you follow the steps in the email. They make it easy for you by having you enter your bank account number and routing number so that they can just transfer the money and you don't have to go through the trouble of writing out an envelope, putting a stamp on it, and mailing a check. They're making this whole process simple, and they're doing it all for you because you just lost your mother and you're still mourning. But what really happens is that instead of $20, they take $2000.
Or, let's add one more spin to this situation. They really do take only the $20 they asked for. You're happy because you just donated to your mother's favorite charity. Now you forget about it. You move on and it's now six months since your mother passed and you notice that someone withdrew $12,000 from your account. How could that have happened?
This is all situational. Yes, the scammers are mean. They don't care about you or your family or your situation. They'll prey upon anyone at any ideal time in order to steal your money.
Scam #3 - Email account hacked
Email account hacking can be tricky. If your email account actually gets hacked, meaning that someone actually gains access to your account and can read all of your emails (and can send emails as you) things may not play out as you'd expect.
For example, a hacker may gain access to your account and the only thing they do is read your email...for six months. And you'll never know it because nothing looks out of place. And then something happens and you realize you've been hacked. But you just can't figure out for the life of you how or when they got in. Realize that they could have gotten in many months ago. Don't beat yourself up. Follow the tips I offered above under "Specific Accounts".
So, as I said, be suspicious about EVERYTHING. Watch for bad websites. Don't trust every email you receive. Be diligent and not gullable.
When I have a problem with my truck, I bring it to my local mechanic who I've been going to for years and who I trust with my vehicles. When I have a pain in my shoulder, I talk to my doctor who I've been going to for years and who I trust with my health. The same must hold true for technology.
There was an email going around years ago that told Windows users that if there was a certain file on their computer, it was a virus and must be removed (CNET still has an article about it). So, recipents of that email did just that. They found the file and removed it, thinking that they were keeping their computer safe. But it was a hoax; and the file is one that Windows needs.
So what was the real problem here? The problem was that these folks trusted some friend who emailed them with technology advice. A friend with no such qualifications. And that friend probably got the info from Aunt Judy and just forwarded the email (no offense to Aunt Judy).
In another example, I just saw a reporter on the news talk about a security issue and end his report by offering cybersecurity tips that had nothing to do with the story he had just reported on. While this reporter may have looked and sounded trustworthy (after all, he was wearing a necktie and had a microphone), he's not.
In yet another example, I see friends on Facebook copy and paste messages about how they can improve the behavior of their feed. "Just copy and paste this to your page and you'll see fewer ads and more relevant posts." THIS DOES NOT WORK. But I'll tell you what it does and why some idiot started it. It's a scam. It's a hacker somewhere testing you to see how gullable you are. If you copy and paste such a message, then YOU might be willing to do even more or YOU might be the kind of person who doesn't keep their accounts secure. Now, YOU are a target for a future scam. And think about it. If you've seen someone do this, that message is probably still there on that person's Facebook account. It's like hanging a sign out in front of your house saying "hack me". They should delete that message now and never do it again. And if you fell victim to this, why? Why did you trust what your Aunt Judy said? What does she know about such things? (Again, no offense to Aunt Judy.)
So, what's the point with these examples? Simple: be careful who you trust with technical advice. You should have a reliable source who you go to for such things (just like you do with your car and your health).
And yes, this goes for me too. Why should you trust me or anything I have to say? Only you can answer that. It's up to you. Choose who you should trust and don't listen to unqualified people offering advice.
Summary
Please understand that there is no single piece of advice that I can offer that will guarantee the security of your accounts and identity. All I can do is offer the above list of recommendations, some of which may apply to you and some of which may not. I can tell you, though, that I follow all of the above tips. But it's up to you to decide what to do for your own situation.
Perhaps you've noticed that much of what I said does not require technical knowledge so much as it requires common sense and awareness of social interactions. Don't worry if you're not that technically-minded. You can do this.
I will update this article periodically as trends unfold and I see new threats. I welcome any feedback or suggestions you have.
Scott Crevier
scott@crevier.org
Orig version: Sat 06-Jan-2024
Last update : Sat 07-Sep-2024